
Securely Accessing SAP CPI Integration from External Systems
Executive Summary
As enterprises accelerate digital transformation, Integration has become a strategic capability rather than a back-office function. Organizations increasingly rely on APIs and cloud-native integration to enable collaboration across partners, customers, and ecosystems. However, securely exposing Integration endpoints—especially within mission-critical SAP environments—remains a complex architectural challenge.
This white paper examines the risks and constraints associated with directly exposing SAP Cloud Integration (CPI) Integration to external systems. It analyzes the architectural limitations, security implications, and compliance considerations, and presents a robust, SAP-recommended solution using SAP Integration Suite and the Process Integration Runtime within SAP Business Technology Platform (BTP).
Designed for IT architects, SAP developers, integration specialists, and business leaders, this paper provides an authoritative, research-backed framework for building secure, scalable, and compliant external integrations.
1. Introduction
In today’s interconnected digital ecosystem, seamless system integration is essential for operational efficiency, real-time decision-making, and business agility. Enterprises are integrating ERP systems, cloud applications, partner portals, mobile platforms, and IoT devices in increasingly complex landscapes.
SAP Integration Suite, which includes SAP Cloud Integration (CPI), provides a comprehensive integration platform-as-a-service (iPaaS) to design, deploy, and manage integration flows (iFlows). However, exposing CPI Integrations to external systems introduces significant security and governance challenges.
SAP explicitly does not support direct internet exposure of CPI runtime endpoints. Attempting to bypass architectural safeguards may result in:
- Unauthorized system access
- Data breaches
- Regulatory non-compliance
- Increased operational risk
This white paper explains why direct exposure is discouraged and presents a secure, scalable architecture leveraging SAP BTP’s Process Integration Runtime as a controlled access layer.
2. Problem Statement: The Risks of Direct CPI Exposure
2.1 The Architectural Constraint
CPI integration flows commonly use HTTP sender adapters to accept inbound requests. These endpoints are technically accessible after deployment but are not intended for direct public exposure. SAP’s cloud-native architecture intentionally separates:
- Integration logic
- Authentication and authorization
- Runtime security enforcement
Directly exposing CPI endpoints violates this separation of concerns.
2.2 Core Technical Challenges
Authentication & Authorization
- Avoid embedding credentials within iFlows
- Support modern OAuth 2.0 token-based authentication
- Enable secure machine-to-machine communication
Scalability & Governance
- Onboard multiple partners securely
- Revoke access without redeploying integrations
- Maintain audit logs and traceability
Regulatory Compliance
Organizations must comply with standards such as GDPR, HIPAA, and ISO 27001. IBM’s 2024 Cost of a Data Breach Report estimates the average breach cost at $4.88 million, underscoring the financial impact of insecure architectures.
Decoupling Security from Business Logic
Security should not be embedded inside transformation flows. Tight coupling reduces maintainability, complicates upgrades, and increases regression risk.
3. Solution: Secure Access to CPI
3.1 SAP BTP Process Integration Runtime
SAP addresses these challenges through a proxy-based access model within SAP Business Technology Platform. Instead of exposing CPI directly, external systems authenticate against the Process Integration Runtime, which securely proxies validated requests to CPI.
This model enforces:
- OAuth 2.0 token validation
- HTTPS-only communication
- Centralized identity management
- Controlled runtime routing
Process Integration Runtime service enables:
- Secure runtime URL generation
- OAuth 2.0 client credential support
- Service key management
- Controlled access per iFlow
Instances are created under the "integration-flow" plan in BTP subaccounts.
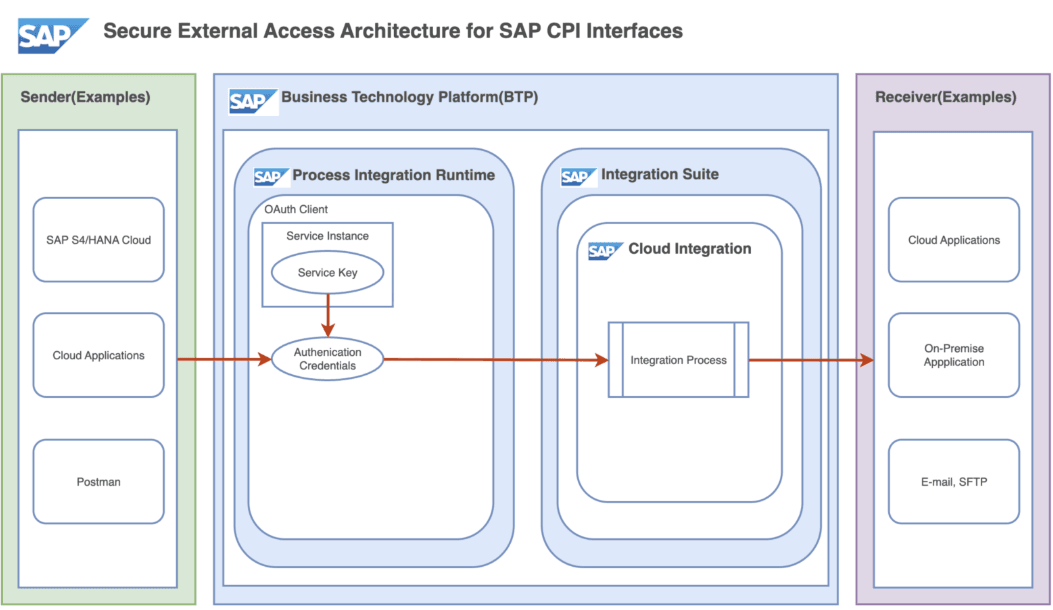
3.2 Security Benefits and Strategic Advantages
Defense-in-Depth
- No direct internet exposure
- Centralized authentication
- Encrypted HTTPS traffic
- Token-based access control
Governance & Auditability
- Access logs captured at runtime
- Traceability for compliance
- Simplified audits
Operational Efficiency
- Faster partner onboarding
- Security changes independent of iFlow redeployment
- Reduced custom gateway development
Scalability
- Cloud-native auto-scaling
- Multi-client support
- Granular entitlement management
4. Real-World Applications
- Manufacturing:Suppliers securely submit purchase orders via OAuth-authenticated HTTP calls.
- Retail:E-commerce systems sync inventory in real time without exposing internal ERP endpoints.
5. Business Impact and ROI
- Risk Reduction:Preventing a single breach can save millions in remediation, regulatory penalties, and reputational damage.
- Faster Ecosystem Enablement:Secure APIs accelerate partner collaboration and digital marketplace participation.
- Reduced Technical Debt:Centralized security architecture eliminates fragile, hardcoded authentication logic.
- Competitive Advantage:Secure integrations enable innovation without compromising governance.
6. Conclusion
Securely accessing SAP CPI interfaces from external systems is not merely a technical configuration—it is a strategic architectural decision.
By leveraging:
- SAP Integration Suite
- Process Integration Runtime
- OAuth 2.0 authentication
- CSRF best practices
- Centralized governance within SAP Business Technology Platform
Organizations can achieve:
- Controlled external access
- Regulatory compliance
- Operational resilience
- Scalable partner integration
As cloud adoption accelerates and API-driven ecosystems expand, mastering this secure access model becomes essential for sustainable digital growth.
Call to Action
To operationalize this architecture:
- Review your current CPI exposure model.
- Validate entitlements within SAP BTP.
- Implement Process Integration Runtime instances.
- Adopt OAuth-based authentication for all external integrations.
For tailored guidance, consult SAP’s official documentation or engage certified SAP integration experts to assess your landscape.
About This White Paper
This document reflects SAP BTP best practices as of the latest platform updates and is intended to support architectural decision-making for secure enterprise integration.
Stay Informed
Get the latest insights on Agentic Engineering and SAP digital transformations delivered to your inbox.